Method And System For Forensic Data Tracking
Patent No. US10999300 (titled "Method And System For Forensic Data Tracking") was filed by Quickvault Inc on Nov 26, 2019.
What is this patent about?
’300 is related to the field of data loss prevention and, more specifically, to systems that track the movement of data elements across authorized and unauthorized devices and users. Traditional security measures like firewalls and encryption often fail to prevent data breaches when data leaks outside the protected environment, for example, via USB drives or unauthorized cloud storage. Existing Data Loss Prevention (DLP) tools are not always effective, leaving sensitive data vulnerable once it escapes the protected environment.
The underlying idea behind ’300 is to embed forensic tracking mechanisms directly into data files, allowing their movement and usage to be monitored even after they have left the control of the originating organization. This is achieved by scanning files, classifying them based on their content, and then encoding them with unique identifiers or watermarks. When these encoded files are accessed, they report back to a central server, providing information about the endpoint, user, and time of access.
The claims of ’300 focus on a cloud-based forensic computing platform that receives metadata logs from endpoints, analyzes the data element tags within those logs, and determines a data classification for the files on those endpoints. The platform then predicts data breaches based on changes in data topology, such as spikes in user activity or data of a specific classification leaking onto unauthorized endpoints. The platform also identifies patterns of data use that constitute rule violations or deviations from normal behavior, such as an endpoint significantly increasing or decreasing its total number of files.
In practice, the invention involves deploying software agents on endpoints that scan files, classify them based on predefined text strings or patterns (e.g., ICD-9 codes for PHI data), and then encode them with forensic information. This encoding can take various forms, including transparent GIFs with embedded URLs, executable components that report back to the server, or printable watermarks. The agents then transmit metadata logs to a central cloud control server, which analyzes the data and generates alerts based on predefined policies and settings.
This approach differs from traditional DLP solutions by focusing on data provenance and providing visibility into data movement even outside the organization's direct control. Unlike encryption-based solutions that become ineffective once the data is decrypted on an unauthorized device, ’300 maintains awareness of the data's location and usage through its embedded tracking mechanisms. By analyzing patterns of data movement and identifying deviations from normal behavior, the platform can proactively predict and prevent data breaches.
How does this patent fit in bigger picture?
Technical landscape at the time
In the early 2010s when ’300 was filed, data loss prevention (DLP) tools were in use, but were not always effective at preventing all sensitive data from leaking outside of protected environments; at a time when encryption was commonly used to protect data at rest and in transit between authorized systems, but tracking data after it left the authorized environment remained a challenge; when hardware or software constraints made comprehensive data provenance and tracking across various devices and cloud storage systems non-trivial.
Novelty and Inventive Step
Claims were rejected under 35 U.S.C. 112(a) for failing to comply with the enablement requirement. Claims were also rejected under 35 U.S.C. 102(a)(1) and 35 U.S.C. 103 as being unpatentable over cited prior art. Claims 1-27 were rejected on the ground of nonstatutory double patenting. Claims 18 and 19 were indicated as allowable. The prosecution record does NOT describe the technical reasoning or specific claim changes that led to allowance.
Claims
This patent contains 25 claims, with independent claims 1 and 25. The independent claims are directed to a forensic computing platform deployed as a cloud control server. The dependent claims generally elaborate on and refine the features and functionalities of the forensic computing platform described in the independent claims.
Key Claim Terms New
Definitions of key terms used in the patent claims.
Litigation Cases New
US Latest litigation cases involving this patent.
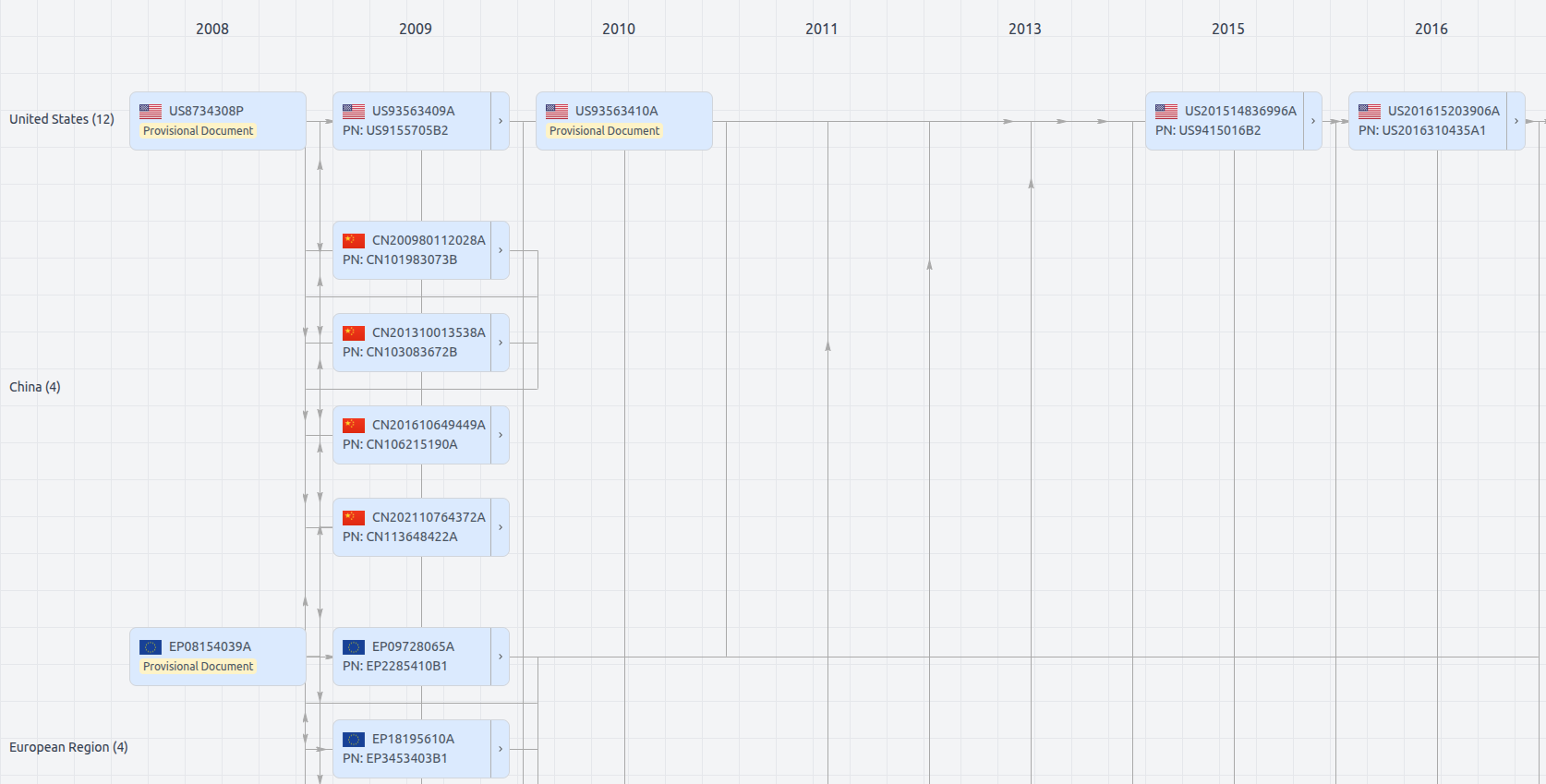
Patent Family
File Wrapper
The dossier documents provide a comprehensive record of the patent's prosecution history - including filings, correspondence, and decisions made by patent offices - and are crucial for understanding the patent's legal journey and any challenges it may have faced during examination.
Date
Description
Get instant alerts for new documents
US10999300
- Application Number
- US16695949
- Filing Date
- Nov 26, 2019
- Status
- Granted
- Expiry Date
- Sep 14, 2035
- External Links
- Slate, USPTO, Google Patents