Classification Management
Patent No. US11044256 (titled "Classification Management") was filed by Appomni Inc on Dec 22, 2020.
What is this patent about?
’256 is related to the field of cloud software and, more specifically, to the management and governance of elements (data, configurations, etc.) stored across multiple Software-as-a-Service (SaaS) platforms. Existing labeling schemes for cloud software lack expressiveness and the ability to reflect the structure of organizations, making it difficult to manage security attributes and ensure governance across various SaaS platforms.
The underlying idea behind ’256 is to provide a customizable classification system that allows users to map elements from different SaaS platforms to a single, centralized classification structure. This involves defining a hierarchy of classifications, associating elements with these classifications, and specifying prescribed security attributes for each mapping. The system then compares these prescribed attributes with the actual configured security attributes to identify discrepancies and potential security risks.
The claims of ’256 focus on a system, method, and computer program product that obtain mappings of stored elements to a plurality of classifications via a user interface. These mappings include prescribed security attributes. The claims further cover obtaining a policy that includes identifying information associated with a set of actors and a specified portion of the classifications. The system then compares configured security attributes of the actors to the prescribed security attributes and outputs information pertaining to any discrepancies found.
In practice, the invention allows an administrator to define a hierarchy of classifications that reflect the organization's structure and security policies. They can then map elements from various SaaS platforms (e.g., Salesforce, Workday) to these classifications, specifying the desired security attributes for each mapping. The system then periodically audits the actual configurations of these SaaS platforms, comparing them to the prescribed attributes. Any deviations are flagged as discrepancies, allowing the administrator to take corrective action.
This approach differs from prior solutions by providing a flexible and centralized way to manage security attributes across multiple SaaS platforms. Instead of relying on each platform's native labeling scheme, which may be limited or inconsistent, ’256 allows users to define their own customizable classifications and mappings. Furthermore, the system automates the auditing process, identifying discrepancies that might otherwise go unnoticed, thereby improving overall security and governance.
How does this patent fit in bigger picture?
Technical landscape at the time
In the early 2020s when ’256 was filed, systems commonly relied on centralized identity and access management (IAM) solutions, at a time when cloud-based services were typically integrated using standard APIs and protocols. When hardware or software constraints made the enforcement of fine-grained access control policies across diverse data sources non-trivial.
Novelty and Inventive Step
The examiner approved the application because the prior art, specifically Grand (US 2020/0184090 A1) and Hopkins et al. (US 2017/0272349 A1), when taken alone or in combination, do not teach or suggest a system with a processor configured to: obtain mappings of stored elements to classifications via a user interface, where the mappings include prescribed security attributes; obtain a policy identifying actors and classifications via a user interface; compare configured security attributes of actors to prescribed security attributes of classifications; and output discrepancy information based on the comparison.
Claims
This patent contains 20 claims, with independent claims 1, 11, and 20. The independent claims are directed to a system, a method, and a computer program product, respectively, all generally focused on identifying discrepancies between configured security attributes of actors and prescribed security attributes of classifications. The dependent claims generally elaborate on and add detail to the elements and steps recited in the independent claims.
Key Claim Terms New
Definitions of key terms used in the patent claims.
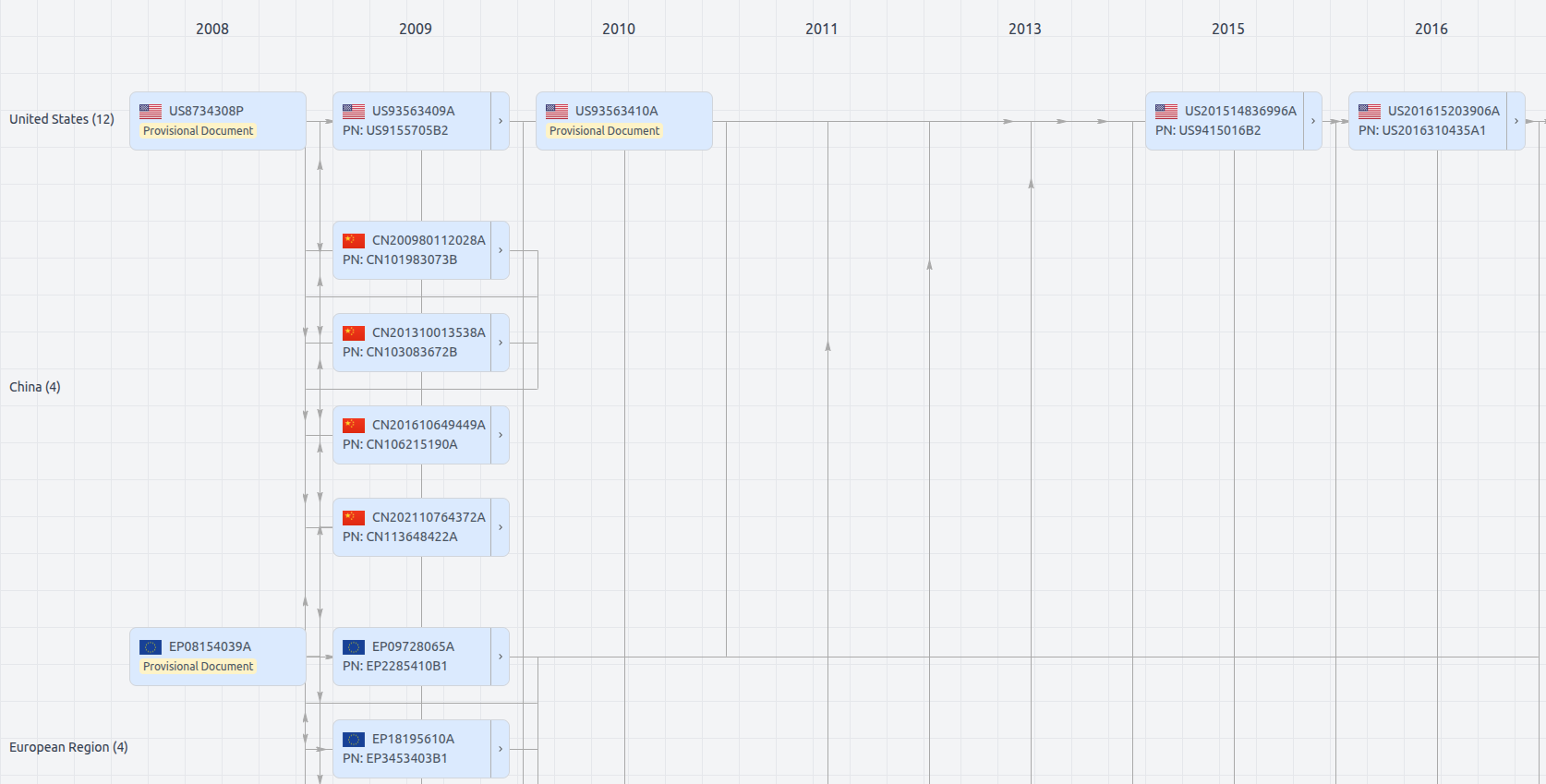
Patent Family
File Wrapper
The dossier documents provide a comprehensive record of the patent's prosecution history - including filings, correspondence, and decisions made by patent offices - and are crucial for understanding the patent's legal journey and any challenges it may have faced during examination.
Date
Description
Get instant alerts for new documents
US11044256
- Application Number
- US17130484
- Filing Date
- Dec 22, 2020
- Status
- Granted
- Expiry Date
- Dec 22, 2040
- External Links
- Slate, USPTO, Google Patents