Mobile Device Enabled Desktop Tethered And Tetherless Authentication
Patent No. US11811750 (titled "Mobile Device Enabled Desktop Tethered And Tetherless Authentication") was filed by Piccadilly Patent Funding Llc As Security Holder on Nov 8, 2021.
What is this patent about?
’750 is related to the field of digital authentication, specifically addressing the problem of securely logging into computing devices like laptops and desktops. Traditional methods often rely on passwords, which can be vulnerable to theft or compromise. Existing solutions using mobile device proximity have limitations, as unauthorized access can occur if a thief gains possession of the mobile device.
The underlying idea behind ’750 is to leverage a mobile device as a secure authentication token for a computer, even when the computer is offline. This involves a cloud-based clearinghouse that links a user's mobile device to their identity. When a user attempts to log in to their computer, a request is sent to the mobile device for authentication, using methods like biometrics or answering security questions.
The claims of ’750 focus on a computer-implemented method involving a cloud universal identification server. The server stores user attributes and associates a mobile device with the user's identity. Upon receiving an authentication request from a computer (via a credential provider), the server confirms the computer's identity, retrieves a communication protocol for the mobile device, transmits an authentication factor to the mobile device, and, upon successful authentication on the mobile device, sends authentication data to the computer to complete the login process.
In practice, a user installs a credential provider on their computer and registers their mobile device with the cloud service. When logging in, the user selects the mobile device authentication option. The credential provider then sends a request to the cloud service, which in turn pushes an authentication challenge to the user's mobile device. The user authenticates on their phone (e.g., using a fingerprint), and the cloud service signals the computer to grant access.
This approach differentiates itself from prior art by providing a more secure and convenient authentication method. Instead of relying solely on passwords or proximity, it uses the mobile device as a second factor authentication , enhancing security. The system also supports offline authentication by using tethered connections like USB or Bluetooth, ensuring access even without an internet connection on the computer itself. The use of a cloud clearinghouse allows for centralized management of user identities and authentication policies.
How does this patent fit in bigger picture?
Technical landscape at the time
In the mid-2010s when ’750 was filed, at a time when systems commonly relied on usernames and passwords for authentication, hardware and software constraints made secure and convenient alternatives non-trivial. Mobile devices were increasingly prevalent, but integrating them seamlessly and securely with desktop authentication, especially in offline scenarios, presented engineering challenges. Federated identity management was gaining traction, but its complexity and maintenance overhead were significant.
Novelty and Inventive Step
The examiner allowed the claims because the applicant incorporated limitations from U.S. Patent No. 11,171,941 B2. These limitations include receiving and storing identifying attributes at a cloud server, receiving a request from credential provider code on a computing device, configuring the credential provider code to recognize the mobile device, and using the mobile device for authentication purposes by retrieving a communication protocol from a database.
Claims
This patent contains 19 claims, of which claims 1, 10, and 19 are independent. The independent claims are directed to a computer-implemented method, an apparatus, and a non-transitory computer readable medium, respectively, all generally relating to authenticating a process on a computing device using a mobile device and a cloud universal identification server. The dependent claims generally elaborate on and refine the elements and steps recited in the independent claims.
Key Claim Terms New
Definitions of key terms used in the patent claims.
Litigation Cases New
US Latest litigation cases involving this patent.
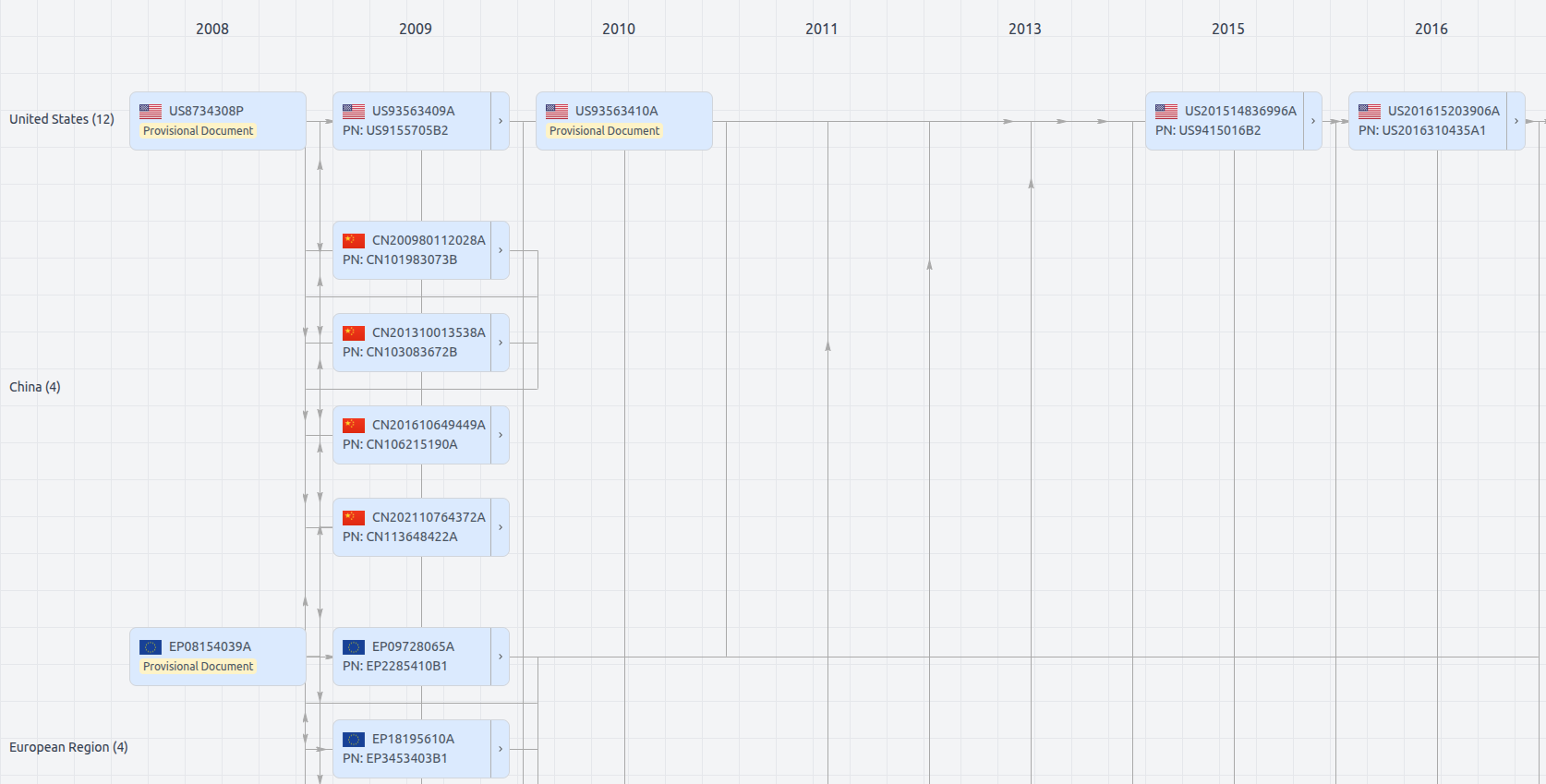
Patent Family
File Wrapper
The dossier documents provide a comprehensive record of the patent's prosecution history - including filings, correspondence, and decisions made by patent offices - and are crucial for understanding the patent's legal journey and any challenges it may have faced during examination.
Date
Description
Get instant alerts for new documents
US11811750
- Application Number
- US17521611
- Filing Date
- Nov 8, 2021
- Status
- Granted
- Expiry Date
- Feb 24, 2036
- External Links
- Slate, USPTO, Google Patents