Smart Edge Co-Processor
Patent No. US11847580 (titled "Smart Edge Co-Processor") was filed by Nusantao Ip Llc on Aug 8, 2022.
What is this patent about?
’580 is related to the field of securing data from sensors in electronic devices. Traditional systems are vulnerable to hacking because sensor data is often processed and transmitted without encryption, leaving it exposed if a device's security is breached. This is particularly relevant with the proliferation of IoT devices and the increasing number of sensors in mobile devices, creating a larger attack surface.
The underlying idea behind ’580 is to push security and encryption to the edge of the network , specifically at the sensor level. This involves interposing a smart edge module between the sensor and the device's main processor. The smart edge module encrypts the raw sensor data before it reaches the processor, ensuring that even if a hacker gains access to the device, they can only access encrypted data.
The claims of ’580 focus on an electronic device comprising a device processor, a device bus, a device memory, a plurality of sensors, a JTAG access point, and at least one security module. The security module, implemented using at least a hardware processor, is interposed between at least one corresponding sensor of the plurality of sensors and the device bus. The security module is coupled to the JTAG access point and configured to execute JTAG interrogation calls to authenticate at least the plurality of sensors. A plurality of secured interfaces are each interposed between a corresponding sensor and the security module and each having connections to the JTAG access point; wherein the JTAG access point and the connections to the JTAG access point are embedded in epoxy.
In practice, the smart edge module intercepts the raw data signal from the sensor, encrypts it using a key, and then sends the encrypted data to the device's processor. The module can also decrypt incoming signals from the processor destined for the sensor. A key aspect is the use of a JTAG dongle within the smart edge module to authenticate the sensor and the secured interface, ensuring that the hardware itself hasn't been tampered with. Embedding the JTAG access point in epoxy provides a physical barrier against tampering.
This approach differs significantly from prior art where security measures are primarily focused on the communication link or the device's processor and operating system. By encrypting the data at the sensor level, ’580 provides an additional layer of security that is independent of the device's overall security posture. Furthermore, the smart edge module can include a pre-processing module to filter and transform the raw data before encryption, reducing the amount of data transmitted and improving efficiency. The use of a smart contract to manage authentication parameters and access control adds another layer of flexibility and security.
How does this patent fit in bigger picture?
Technical landscape at the time
In the late 2010s when ’580 was filed, sensors were typically implemented using analog or digital signals accessed over a serial bus with a C-level API, at a time when sensor data was commonly provided in a raw format requiring substantial pre-processing. At that time, hardware or software constraints made it non-trivial to perform significant data processing or security measures directly at the sensor level, when systems commonly relied on processing and securing sensor data at the device level or in the cloud.
Novelty and Inventive Step
The examiner allowed the claims because the prior art does not disclose or make obvious the specific claim limitations recited in independent claim 1, particularly the functional limitations recited in the amended independent claim 1. The examiner stated that the dependent claims, which further limit the independent claims, are also allowable because they are definite and enabled by the specification.
Claims
This patent has 3 claims, with claim 1 being independent. Independent claim 1 is directed to an electronic device with a security module that uses JTAG interrogation calls to authenticate sensors. Claims 2 and 3 are dependent and generally elaborate on the features of the security module described in the independent claim.
Key Claim Terms New
Definitions of key terms used in the patent claims.
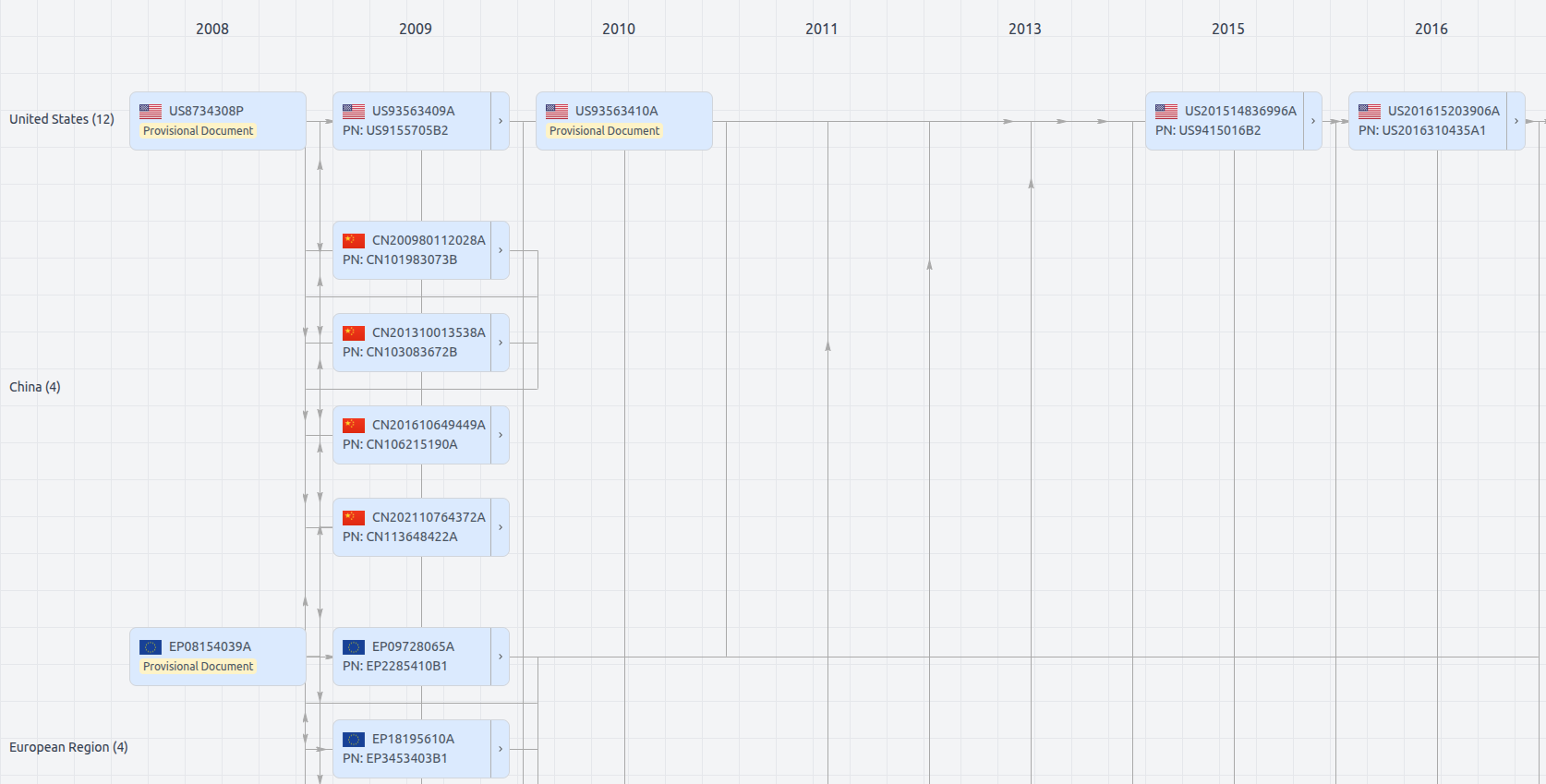
Patent Family
File Wrapper
The dossier documents provide a comprehensive record of the patent's prosecution history - including filings, correspondence, and decisions made by patent offices - and are crucial for understanding the patent's legal journey and any challenges it may have faced during examination.
Date
Description
Get instant alerts for new documents
US11847580
- Application Number
- US17883318
- Filing Date
- Aug 8, 2022
- Status
- Granted
- Expiry Date
- Apr 2, 2040
- External Links
- Slate, USPTO, Google Patents