Correlating Network Event Anomalies Using Active And Passive External Reconnaissance To Identify Attack Information
Patent No. US12301627 (titled "Correlating Network Event Anomalies Using Active And Passive External Reconnaissance To Identify Attack Information") was filed by Qomplx Llc on Sep 20, 2024.
What is this patent about?
’627 is related to the field of cybersecurity and threat analytics, specifically addressing the challenge of understanding and mitigating cyberattacks within complex network environments. Existing cybersecurity rating methods often fail to adequately profile and rate organizations because they don't incorporate sufficient information about the organization's infrastructure, operations, and the relationships between network components. The patent aims to improve the identification of attack patterns and points of origin by correlating anomalous network events.
The underlying idea behind ’627 is to create a cyber-physical graph that models an organization's entire infrastructure, including network devices, users, data assets, and their interrelationships. By analyzing this graph in conjunction with real-time network event data, the system can identify anomalous events, trace attack pathways, and pinpoint the origin of attacks. The key insight is that understanding the relationships between network entities is crucial for effective threat detection and mitigation.
The claims of ’627 focus on a computer system that stores a representation of a directed graph in hardware memory. This graph comprises nodes representing entities (accounts, resources) and edges representing relationships between those entities. The system receives streaming data about network events, identifies new entities and relationships not already in the graph, modifies the graph to include them, and then uses the updated graph to identify potential attack paths involving the new entity. Finally, the system generates a report identifying the involved entities.
In practice, the system continuously monitors network traffic and security logs, identifying deviations from normal behavior. When an anomaly is detected, the system uses the cyber-physical graph to trace the potential attack path, identifying which resources are at risk and how the attacker might be moving through the network. This allows security teams to quickly understand the scope of the attack and take appropriate action to contain it. The system also uses machine learning to refine its understanding of normal behavior and improve its ability to detect anomalies.
The invention differentiates itself from prior approaches by combining real-time network monitoring with a comprehensive model of the organization's infrastructure. Traditional security systems often rely on signature-based detection or simple anomaly detection, which can be easily bypassed by sophisticated attackers. By using a cyber-physical graph, the system can identify attack paths even when the individual events are not inherently malicious. This approach provides a more holistic and proactive approach to cybersecurity, enabling organizations to better protect themselves from evolving threats.
How does this patent fit in bigger picture?
Technical landscape at the time
In the mid-2020s when ’627 was filed, cybersecurity systems commonly relied on graph databases and real-time data analysis to detect and mitigate network threats. At a time when anomaly detection was typically implemented using machine learning algorithms, systems commonly relied on distributed computing architectures to handle large volumes of network data. Hardware and software constraints made real-time graph analysis and anomaly correlation non-trivial.
Novelty and Inventive Step
The examiner allowed the claims because the prior art, specifically Neil and Altman, did not disclose the specific combination of limitations recited in the independent claims. These limitations include identifying an attack path based on a modified graph representation, where the attack path involves identifying a second and third entity reachable from the first entity, and generating a report identifying these entities. The examiner also noted that Neil discloses "detecting anomalous behavior in a network" and Altman teaches “detecting online attacks,” but neither reference teaches the specific combination of limitations in the claims.
Claims
This patent contains 28 claims, with independent claims 1 and 18. The independent claims focus on a computer system that uses graph representations of entities and their relationships to identify attack paths based on streaming data. The dependent claims generally elaborate on specific aspects of attack path identification, graph modification, event analysis, and system configurations.
Key Claim Terms New
Definitions of key terms used in the patent claims.
Litigation Cases New
US Latest litigation cases involving this patent.
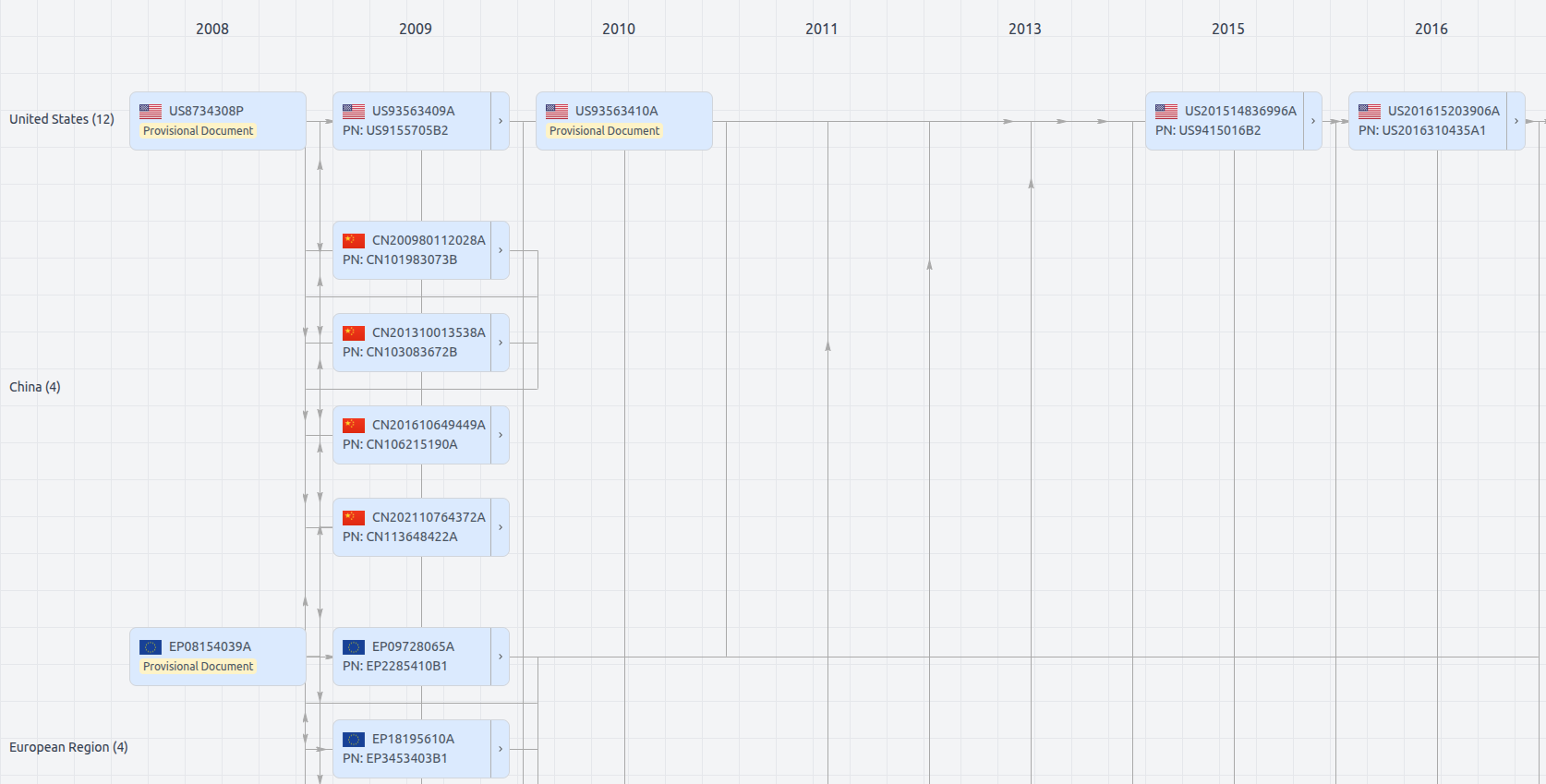
Patent Family
File Wrapper
The dossier documents provide a comprehensive record of the patent's prosecution history - including filings, correspondence, and decisions made by patent offices - and are crucial for understanding the patent's legal journey and any challenges it may have faced during examination.
Date
Description
Get instant alerts for new documents
US12301627
- Application Number
- US18892283
- Filing Date
- Sep 20, 2024
- Status
- Granted
- Expiry Date
- Oct 28, 2035
- External Links
- Slate, USPTO, Google Patents